Describe Two Basic Functions Used in Encryption Algorithms
Hashes are created with an algorithm or hash function and people commonly use them to compare sets of dataSince a hash is unique to a specific message even minor changes to that message result in a dramatically different hash thereby. We discuss these two basic types of encryption technology in the following sections.

Distribution Channels Types Functions And Examples Fourweekmba Marketing Mix Event Planning Quotes Business Binders
Two basic functions used in Encryption Algorithms are Substitution Transposition What algorithm is used to scramble data into a format that can be read only by reversing the algorithm.

. Given the same key and the same input text the algorithm will always return the same encrypted result. Encryption methods are usually categorized as either symmetric or asymmetric depending on the number of keys that are used. 32 What are the two basic functions used in encryption algorithms.
What are the two general approaches to. Elements in the plaintext are rearranged. Use a try block to perform the s.
Why is it not desirable to reuse a key in encryption using a. What are the advantages and disadvantages of triple DES. The first encryption method called hashing creates a unique fixed-length signature for a message or data set.
What are the two basic functions used in encryption algorithms Substitution each from COMPUTER 1140 at American College of International Academics Lahore. A key is simply a known. Without knowledge of the algorithm and the decryption key however the encrypted text is merely a jumble of meaningless information.
25 What are the two general approaches to attacking a cipher. What are the two basic functions used in encryption algorithms. Describe the data encryption algorithm for 64-bit length plaintext and 56-bit length key.
There are many asymptotic notations like 0. The two basic functions used in encryption algorithms are Substitution Transposition 3. The key the input and the cryptographic algorithm are all required.
What are the two basic functions used in encryption algorithms. ArithmeticException is thrown when a division by zero happens. Is a distribution system a wireless network.
AES and 3DES are the approved symmetric-key algorithms used for encryptiondecryption services. 22 What are the two basic functions used in encryption algorithms. Each element in the plaintext is bit letter group of bits or letters is mapped into another element transposition.
Public and private keys. It must be used in conjunction with an encryption algorithm a process or calculation to produce the cipher text. What is the difference between a block cipher and a stream cipher.
This is the readable message or data that is fed into the algorithm as input. The notations show the order of growth of functions. Differentiate between secret-key encryption and public-key encryption.
Here the time taken by an algorithm is mapped regarding mathematical functions. Both use a key or keys to encrypt and decrypt information. What services are provided by WSP.
How many keys are required for two people to communicate via a symmetric cipher. 23 How many keys are required for two people to communicate via a symmetric cipher. What are the two basic functions used in encryption algorithms.
Use another catch block to catch any InputMismatchException and output an exception message with the toString method. What are the two basic functions used in encryption algorithms. Asymptotic Notations are used to describe the execution time of an algorithm.
Elements in the plaintext are rearranged. Encryption provides confidentiality of data by transforming the plaintext into ciphertext. What are the two basic functions used in encryption algorithms.
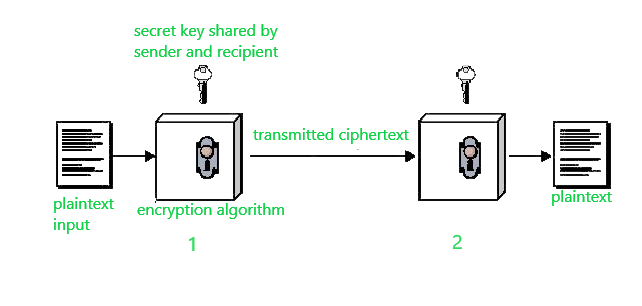
Plaintext Encryption algorithm Secret key Cipher text Decryption algorithm 2. What are the two basic functions used in encryption algorithms Answer the following question. Decryption transforms ciphertext back to plaintext.
A symmetric cipher encryption has five ingredients. Each element in the plaintext bit letter group of bits or letters is mapped into another element Transposition. Use a catch block to catch any ArithmeticException and output an exception message with the getMessage method.
Symmetric and Asymmetric Public Key. Why is the middle portion of triple DES a decryption rather than an encryption. There are two basic methods of encryption.
This is a pair of keys that have been selected so that if one is used for encryption the other is used for decryption. List and briefly define the SSH protocols. Describe the main requirements for the secure use of symmetric encryption.
24 What is the difference between a block cipher and a stream cipher. Answer All encryption algorithms are based on two general principles. The encryption algorithm performs various transformations on the plaintext.
Basic Methods of Encryption.

Guide To Centralized Cryptocurrencies Impacts Of Centralization Blockchain Blockchain Technology Crypto Currencies

French Police Seized Tor Relays In Wannacry Investigation Deep Dot Web Https Www Deepdotweb Com 2017 06 Traffic Analysis Science And Technology Networking

Pin On Data Security And Encryption In Hindi Urdu

20 Top Free Office Software Free Office Software Software Microsoft Office Online

What Types Of Encryption Are There Ico

1 Cryptography And Network Security Third Edition By William Stallings Lecturer Dr Saleem Al Zoubi Cryptography Computer Security Encryption Algorithms

What Is Zero Knowledge Proofs By Jai Infoway Blockchain Cyber Security Awareness Cryptography

Java Object Oriented Programming Build A Quiz Application Udemy Coupon 100 Off Object Oriented Programming Coding Tutorials Writing Programs

What Is Md5 Hash And How To Use It Hashing Cryptography Cyber Security

Block Cipher In A Feistel Cipher The Block Of Plain Text To Be Encrypted Is Split Into Two Equal Sized Halve Cryptography Block Cipher Encryption Algorithms

Quantum Computers Could Greatly Accelerate Machine Learning Quantum Computer Machine Learning Artificial Intelligence Machine Learning
Symmetric Key Algorithm In Cryptography By Quantum Backdoor Medium

April 2015 Question Paper Bscit Question Papers Bscit Semester V Question Paper Network Security Mumbai Bscit Study Question Paper Assumptions Semester
Conventional Encryption Geeksforgeeks

What Is Encryption Explanation And Types Cisco

Everyday Cryptography Ebook By Keith M Martin Rakuten Kobo In 2022 Cryptography Fundamental Computer Programming

Simplified International Data Encryption Algorithm Idea Geeksforgeeks

Algorithm Algorithm Flow Chart Euclid

Encryption Algorithms Explained With Examples Encryption Algorithms Cryptography Computer Security
Comments
Post a Comment